HOME USER COMPUTER SECURITY PRIMER
I've had contact with a few folks
recently who have been hit by one variation or another of the nastiness out in
our personal computing world, and being an IT security professional I know
better than most the level, numbers and frequency that these malicious objects
are being created and circulated - all looking for unsuspecting users'
computers to inhabit.
Many 'typical' home users aren't aware
of many of the more creative means by which these are being propagated, so I
decided to put together a basic primer in order to help my friends cope with
today's Internet vulnerabilities. LONG GONE
ARE THE INNOCENT DAYS WHEN USERS COULD JUST SURF THE NET OR READ EMAIL
UNIMPEDED AND WITHOUT FORETHOUGHT!!!
TYPES OF MALWARE
For the sake of this article I'm going
to group everything nasty into the term malware for the
sake of simplicity. This is not technically correct, but is certainly more
proper (to me for a less-technical audience) than lumping them into the term virus,
because much of what is out there is not viral in nature.
Malware includes Adware, Nagware,
Spyware, keystroke loggers, "unwanted programs", worms, bots,
zombies, boot sector infectors, virii, phishing, etc...
there are a whole plethora of types of nastiness out there in today's computing
world, and much of it is just waiting to bite all of us at the first
opportunity.
One of the worse ones in recent history
is Conficker - it has been extremely effective, has infected 10's of millions
of PCs, and is still estimated to be present on over 6 million
PCs worldwide! This stuff is getting more and more sophisticated and
prevalent. In the last 30 days alone, there have been over 175,000 targets, over 1,000,000 sources, and
over 400,000,000 reports just to the SANS Internet Storm Center
(http://isc.sans.org/submissions.html) alone!!! On any given day there are a
mind-boggling number of new threats released, to add to those existing which
just never seem to die.
A great write-up of the real-world
exploit state is available on SANS at http://www.sans.org/top-cyber-security-risks/,
and is really worth the viewing even for those who aren't technically oriented
or interested... it is a real eye-opener!
Also, an extremely good and
comprehensive list of means to protect yourself is available on SANS at
http://www.sans.org/tip_of_the_day.php
This is by no means meant to be a
complete reference, and while it is extremely lengthy please do us all a favor
and read through this in its entirety - I took the time to put this together
because I care for all of you and would like to help prevent any abuse of my
friends!
EMAIL
Quite some time ago know, some
enterprising black hat-types figured out that email was one of the best means
to circulate their nefarious codes. First it was fairly blatant and rudimentary
- attach an infected file to an email and blindly distribute it to the masses
(SPAM). Now, they've become much more sophisticated and successful by passing:
·
URL links/Phishing
·
Infected PDF or graphic files (often
pornographic, "cute" or of emotional interest)
·
e Cards
The most diabolical aspect of email
distribution was when "they" figured out, through the programming
power of APIs exposed by the email interfaces, it was simple to programatically
compose and send emails to everyone listed in users' personal address books
automatically, so that the email appears to be legitimately sent from a
friend instead of being spam from an unknown source. This has by far caused
the email distribution of malware to become one of, if not the,
most effective means to infect. TAKE NOTE
- JUST BECAUSE IT COMES FROM SOMEONE YOU KNOW DOESN'T MEAN IT WON'T HURT YOU! I can't stress this enough!
Another really cool 'feature' that has
become a popular exploit is to embed a URL link in an email... very benign and
innocent in appearance, and usually appearing to lead to a legitimate website
of interest. This is the heart of the phishing schemes also -
emails sent requesting you to 'update your information' for: banking, credit
cards, Paypal, IRS, etc. NEVER click a link in an email taking you to a
site where you are required to provide login credentials or personal
information, PERIOD!!! If B of A asks you to update your account
information or make a late payment via email, open your browser on your own,
log in to your account, and then take care of whatever business you need to
from there.
Here's an example of how simple it is to
spoof a URL: http://www.microsoft.com The link to the left appears to lead to Microsoft, but if
you click it you will find that is not the case! The scammers are very adept at
downloading all the page graphics from banks and other commerce-type sites and
setting up a fake front, which appears to be legitimate, but which they have
complete control over and can capture any data entry including logon
credentials, account information, etc.
While we're reviewing URL vulns, ALWAYS
check the address bar in your browser to verity you're on the site you
think you are... be sure there are no typos, and if you're making online
purchases be sure the address begins with https ![]() (Windows
XP Pro)
(Windows
XP Pro) ![]() (Windows Vista), and for IE that
the "lock" appears in either the address bar or
status bar (THE STATUS BAR IS YOUR FRIEND!!!), depending on the version
of browser you're using:
(Windows Vista), and for IE that
the "lock" appears in either the address bar or
status bar (THE STATUS BAR IS YOUR FRIEND!!!), depending on the version
of browser you're using:
![]() {Windows XP Pro)
{Windows XP Pro)
![]() (Windows Vista)
(Windows Vista)
This ensures that you are using a HTTPS
connection, which is secured via SSL (Secure Socket Layer) to validate and
encrypt the authentication (a really good thing!).
Regardless of whether you're following a URL
link from an email or a website, you must review the actual link
to verify that it is going to take you to where you think you're going!!! In
most browsers, this is easy to do by hovering the mouse cursor over the URL,
and the actual address should be displayed in the bottom status
bar.
Another common place you will find spoofed
URL addresses is in the social networking sites - Myspace in particular is rife
with these... more on this vulnerability later.
WEBSITE BROWSING
These days, extreme caution needs to be
exercised while innocently browsing the Web... many pitfalls await. Between
downright malicious sites, hijacked sites, DNS spoofing, 'bot networks, and
poisoned search results, it is all too easy to get caught on a "bad"
site and not even realize it. Now days, there are many ways to download and
install the bad stuff without you even knowing it just by going to the 'wrong'
site (even though it appears proper or innocent), and to make matters worse you
may not even know it for days, weeks or even months. Several malicious packages
can now be silently installed just by visiting an infected site, and will lay
dormant on your PC for a long period of time before acting up.
- BE SURE YOU TYPE THE RIGHT DOMAIN
QUALIFIER!
One way that the 'bad guys' are getting over is to purchase a domain
name such as www.visa.net, and to put up a fake front with all the correct
graphics, then drive traffic to the site via means like spam with a URL link,
performing a XSS cross-site scripting attack, or many of the other means to get
users to the website. WWW.VISA.COM is NOT the same as WWW.VISA.NET!!!
As mentioned above, now it is extremely
important to be mindful what sites you choose to visit when doing a Google or
Yahoo search - the search results can be poisoned and malicious fake sites can
be bumped in the website ratings so that they are listed towards the top
results... they appear to be legitimate, have related text displayed in the
results, and can be just informational pages or shopping storefronts designed
to steal your financial information for their own use.
SOCIAL NETWORKING SITES
With the advent of Myspace, and now
Facebook and Twitter, new distribution means have been made available to those
with ill intent, populated by millions of innocent and naive users, just
waiting to fall victim to their evils.
One of the most common Myspace
vulnerabilities I see on an extremely frequent basis is a Friend Request or
Message from an unfamiliar person (very often a good looking chick asking for
you to stay in contact on Myspace or one of the other Instant Messaging tools,
or directing you to another website where you can 'view' their webcams). First
and foremost, if the redirection is to a legitimate site it is
going to be for money and the intent of hooking the user into their "adult
webcam" business. HOWEVER,
many of the profiles are fake yet appear as legitimate Myspace profile pages.
When you hover your mouse cursor over part, or all, of the profile page you
will note that the address in the status bar (THE STATUS BAR IS YOUR
FRIEND!!!) doesn't point to Myspace at all... it will typically redirect
you to an adult-oriented site which also may be compromised or serving up
spyware, virus code, fake AV, adware, etc.... DON'T DO IT!!! Here's an
example for reference:
The address is a legitimate Myspace URL:
![]() (Windows XP Pro)
(Windows XP Pro)
![]() (Windows VISTA)
(Windows VISTA)
The mouse cursor is hovering over the
Profile link:
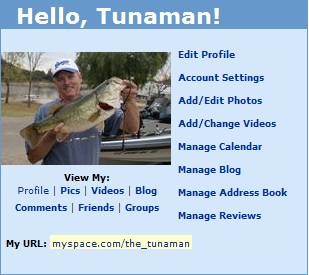
The status bar reveals that the URL link
will indeed take you to a page on Myspace, not some external website:
![]()
Here are some good reference websites
for more information, for whatever social networking sites you're interested
in:
MYSPACE
(So
many vulnerabilities I haven't found one source for a summary listing! Do a
Google search for Myspace vulnerabilities and just review the shear number of
returns!)
FACEBOOK
http://blogs.zdnet.com/security/?p=1414
TWITTER
http://blogsecurity.net/social-networking/twitter-vulnerability-history
http://www.informationweek.com/news/internet/social_network/showArticle.jhtml?articleID=216000011
http://security.vpit.txstate.edu/awareness/social_networking/twitter.html#
UNPROTECTED PORTS
All computer to computer and computer to
server communications are done through things called ports... they are channels
in the operating system which are used to communicate to applications,
interfaces and devices. Many of the more experienced home users remember the
days of modems and that they have to set them up to use a
Ports, however, can be an extreme
vulnerability if not properly controlled and managed. This gets a bit
challenging, as the regular casual use doesn't have the means and understanding
to really do so. Fortunately there are a few methods to protect yourself
without having to obtain a Computer Science degree... Firewalls, Router
configurations and many Antivirus tools can plug many holes without having to
understand the underlying technology - be sure to take whatever measures
you're comfortable with to mitigate as much risk as possible! Suggestions
are included below.
I'd bet few, if any, reading this primer
are aware that there are now several extremely popular and successful
vulnerabilities that are completely transparant and will infect a computer
strictly by being on the Internet via an open and unsecured port! This is one
of the most important reasons to ensure that your operating system,
application and antivirus patches are kept as current as possible! When
building/rebuilding a new computer I will never get it on the network until I
get the patching current, and functional antivirus installed. Current "time to infection" for a Microsoft PC is now
4 minutes or less! All this without
ever surfing the 'Net, reading an email, or doing any action what so ever! For a home network, once a nasty has made it onto one PC it
is usually fairly trivial to infect the rest, many times regardless of the
additional safeguards you've taken. This is especially true for those who are
running with elevated privileges - Administrator, Power User, etc...
BEST PRACTICES
First and foremost, as mentioned
previously PATCH YOUR COMPUTER and ENSURE YOU HAVE FUNCTIONAL, UP-TO-DATE
ANTIVIRUS SOFTWARE INSTALLED AND RUNNING! Be sure your computer is set to
receive (minimum) and install (preferred) all Microsoft patches as they
become available, and that your AV software is also set to update DAILY!!!
This also goes for your applications and "helper applications" - MS
Office, Adobe Acrobat, photo editing software, banking software, Quicktime,
Adobe Flash, etc.
Also be sure your AV software is set to
perform a complete scan REGULARLY... once a week is minimum, more often
is better. Be sure to let it run to completion - overnight is probably best so
that it doesn't impact your computer's performance when you're using it. And
make sure the default settings appear to be correct - DO NOTHING is not
a good response when something is discovered! Minimal is to quarantine and
notify, better is to set to CLEAN, then DELETE if unable to clean!
Be sure whatever available security is
turned on for your router or cable/DSL modem - that will prevent much from
getting onto your home network.
Realizing it is a PITA (pain in the
arse), DO NOT use administrator-level user accounts for your daily use, PERIOD.
This just opens up your computer to whatever is out there, as much of the
vulnerability code will execute in whatever user context is current.
Be sure you have Windows Firewall
turned on, or are using some other software or hardware firewall! This will
stop much of the bad stuff at the gate, as far as what is dynamically being
thrown at you - it will not however prevent much of what you bring on to
yourselves via surfing, email, etc... it is just one more measure to take
towards minimizing your risk and exposure!
Be sure Windows Defender is also
set to automatically update, or at least notify so you can manually update, and
that it is also scheduled to run on a REGULAR basis... Daily isn't
unreasonable, as I don't find it to be as resource-intensive as AV software is.
RECOVERY
OK - so now that you've gone and secured
your systems, you find that there is some nastiness present... or you ignored
all of my warnings and got yourself in trouble... OR set this primer aside to
read later because I wrote so much and didn't get a chance to take the
precautions I've tediously laid out, and you now need to know how to get your
system back (IF POSSIBLE!!!). Yes, there
are a great many circumstances these days where you just may not be able
to recover! Unfortunate but true.
DO NOT CALL ME!!! And especially DO NOT EMAIL ME!!! Just
kidding, sort of, but the intent here is to provide you with many of the means
to heal thyself... and besides, I don't live close to most of you now, so I
probably won't be of a lot of use - try these first, THEN get a hold of
me for further consult if you are still FUBAR.
FIRST THING TO DO, regardless whether
you're infected or not, is to develop and implement a BACKUP PLAN and do
so REGULARLY! BACK YOUR IMPORTANT STUFF UP!!! Digital photos are
priceless, and it is all too easy to lose YEARS' worth of photos
forever! Quicken/Money data files are IMPORTANT - BACK THEM UP! I'm not
going to go into data backup strategies, as that is a whole 'nother primer and
as it is you're going to be challenged to read all of this! Suffice it to say,
whether it is to removable media (CD/DVD/tape/floppy media), another computer
or two or three, digital memory -
That being said, here are a few
resources you can use to attempt recovery for vulnerabilities you might
encounter:
MSRT -
Microsoft has developed the Malicious Software Recovery Tool for aiding with
identifying and remediating any malicious software your computer might be
hosting. To check to see if it is already installed, Click Start | Run
and enter "MRT" in the Open dialog box, then press Enter
- if it already exists, the opening screen will be displayed. IF YOU DON'T
HAVE IT, GET IT! It's free, doesn't take much in the way of computing
power, and will help protect your system and recover if you do happen to get
hit! You can also access and execute it from Microsoft's site, in a pinch.
MSRT information: http://support.microsoft.com/Default.aspx?kbid=890830
MSRT Download page: http://www.microsoft.com/security/malwareremove/default.aspx
McAfee recovery tools: http://vil.nai.com/vil/averttools.aspx
(Stinger is one of the best freeware removal tools available - first
thing I'll grab myself)
Symantec recovery tools: http://www.symantec.com/norton/security_response/removaltools.jsp
Sophos virus removal instructions: http://www.sophos.com/support/disinfection/
(detailed step-by-step instructions on how to remove specific virii should you
know what you're now infected with)
Sophos Threat Detection Test: http://www.sophos.com/products/free-tools/sophos-threat-detection-test.html?utm_source=Non-campaign&utm_medium=Cross%20link&utm_campaign=Disinfection-TDT-promo
(no endorsement implied, as I haven't personally tried it out. However, knowing
that Sophos is one of the industry leaders I have confidence in including the
link here... this can be used to examine your system, as well as test your
non-Sophos antivirus software(s) apparently)
Bootsector Infectors - if somehow you've gotten infected with a bootsector
infector (you see the word bootsector or rootkit in any of the alerts for
instance), this is a BAD THING and can be extremely nasty to deal with. This
means malicious code has been loaded deep down in your computer, before control
has even been passed to the operating system. Reloading Windows, running the
recovery tools, and crying probably won't be able to recover from it... it will
likely require a low-level format of the hard drive (wiping EVERYTHING -
you DID back up your system, right???) and reinstallation of the
operating system and all applications and settings. Many/most of the newer
computers now come with recovery images on the hard drive (in a separate
partition, usually hidden) where the system can be restored to a virgin
image... you will lose all customizations, all applications you've installed
since you first got it, and things like pictures, audio files, etc... ANYTHING
that wasn't on it when you first got it (YOU DID BACK IT UP, DIDN'T
YOU???). Most of the time it will require delicate surgery (from the hands of a
skilled computer person) to get the system cleaned and recovered, as it may
likely require the Primary partition to be formatted at very least, and in
worst case it will require all the partitions to be wiped and recreated, thus
also removing the recovery image. TAKE THE
TIME, at your earliest convenience, to MAKE THE RECOVERY DISCS if your computer
provides the facility... this will make a copy of the recovery image files on
CD or DVD media IN CASE THE DRIVE IS TOAST or otherwise requires Draconian
voodoo magic (low-level formatting and partitioning). Final warning and recommendation.
Good luck, and hopefully if you follow
the information I've outlined above, you won't have to attempt the measures
I've outlined towards the end!
Happy computing!!!!
Tunaman